Night Walker
#Keylogger #Dropper
Name: N1ght_Walker.exe Size: 99.50kb
Type: executable OS: Windows
Hash: 2ca75523249a86484a6dd5517999cae634899d8975fcd8ddad422f4ecae205ca
Summary
Running the executable will drop 1 file called ‘Secret_log.txt’ and then will run in the background to get 40 keystrokes, once the executable get the 40 keystrokes it will encrypt them with AES CBC Mode algorithm and save the encrypted text to ‘Secret_log.txt’ file and then it will terminated from the background.
So we should identify the Algorithm, Key & IV and write a small script to brute force the last 2 bytes of the key to get the final decrypted text.
Methodology
1. Basic Static Analysis
2. Basic Dynamic Analysis
3. Advanced Static Analysis
After downloading ‘N1ght_walker.rar’ and extracting it, we can see there are 2 files, ‘N1ght_Walker.exe’ and ‘flag.txt’ .
1-Basic Static Analysis
By identifying the type of the 2 files I got that: ‘N1ght_Walker.exe’ is PE32 executable for windows and ‘flag.txt’ seems to be encrypted text file as we can see in this image:
So let’s extracting the metadata from N1ght_Walker.exeusing [Strings – Resource Hacker – PeStudio – Capa - ExeinfoPE] …
1. Strings
I found some interesting strings in these following images:
Secret_log.txt -> interesting file name
bcrypt.dll -> Windows Cryptographic API
Now we know that this executable may encrypt something in the Space xD
I tried to see any resources into the file by Resource Hacker but “nothing” So i went for PeStudio to get more details about it...
2. PeStudio
As we can see in the next image, the file is not packed because there is no a big difference between raw-size and virtual-size...
3. Capa
By identifying the capabilities in our executable using Capa to know more about its behavior, we got something interesting...
The executable seems to be a Keylogger !
4. ExeinfoPE
Trying to know more about the signature of the executable using ExeinfoPE...
Ok it is a 64bit executable and as we said in the Step2 the file is not packed.
Before going to Advanced Static Analysis I need to know more about its behavior so let’s go for Basic Dynamic Analysis...
2- Basic Dynamic Analysis
· Procmon
Process Monitor show that the executable dropped a file called Secret_log.txt
The executable console disappeared so I checked the new file ‘Secret_log.txt’ and I noticed that it is empty.
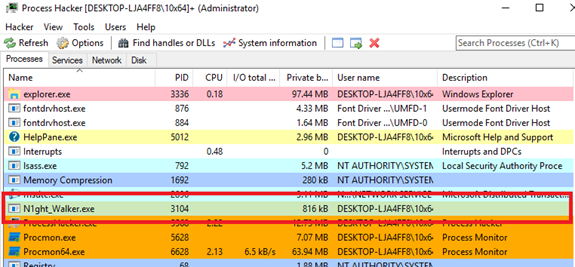
I used Process Hacker to sure that the executable is not running in the background but guess what? It is running :D
So I should go for Advanced Static Analysis now to know what happened...
3-Advanced Static Analysis
Using IDA to check the instructions and search for anything interesting...
Ok I took 5 minutes to get the main function from the entry point after searching for the file name ‘Secret_log.txt’ which the executable dropped it before and I got this function in the image so I follow its xrefand I found that the executable uses ShowWindows API to hide itself and call the function sub_140001104 using the file name ‘Secret_log.txt’.
So let’s follow sub_140001226 function...
Then go sub_140003E90 and I found this function is very interesting because there is a Windows API called SetWindowsHookExW so have to search about it on Google...
Here is the syntax of this API, (idHook, lpfn, hmod, dwThreadId)
According to the last function which has: result = SetWindowsHookExW(13, fn, 0i64, 0);
I found idHook parameters value in the same website so 13 represents to a Keylogger.
We can identify that fn is a function, so by following it we will see that it calling another function called sub_140003E20...
After following it we get this:
Ok it calls sub_140001339 function and if you follow it you will reach this function which is for key logging:
After checking this function I found that the function will take only 40 keystroke and after that generate a number between 0 to 120 in the loop and then put them on pbSecret[i] so I think this is a part of key so we can jump to its xrefto see which functions used it:
Wait, it means that the executable which is running in the background logged the keystrokes I did and then terminated automatically, so I back to the file ‘Secret_log.txt’ and I found it contains encrypted text !
Let us back to IDAagain check the functions that we jumped into it:
By checking this function I found an interesting and special something:
There is BCrypt Windows API which uses AESCipher for the encryption!
From the last 2 images we can notice that the cipher is AES with CBC (Cipher Block Chaining) mode.
Following unk_140011DE8 to check the data and we got that:
Notice that the last 2 bytes of the key are random and iv is from 0 to F so we can brute force the key for all possible values and try to search the word ‘Window:’ in the result.
So I wrote this simple script to get the clear flagwithout any useless strings:
Running it...
And we got the flag J.
You can find the script Here .