you_bee_ex
Name: you_bee_ex.exe Size: 14.3kb
Type: executable OS: Windows
Sha1: 058A5CC996F7CA946C037574FD14AD817E6B5939
Summary
The executable is packed and after analysis we can identify that it requires 101~104 arguments to return something, it uses GetModuleFileNameAwindows API to get the pass of the file then xor all characters from the path with a constant value and finally print the text.
So let’s extract the metadata from it using [Strings – Resource Hacker – PeStudio – Capa] …
1. Strings
Using Strings to see any important or interesting string but nothing important I think...
2. Resource Hacker
Trying Resource Hacker but the same as strings, still nothing...
3. PeStudio
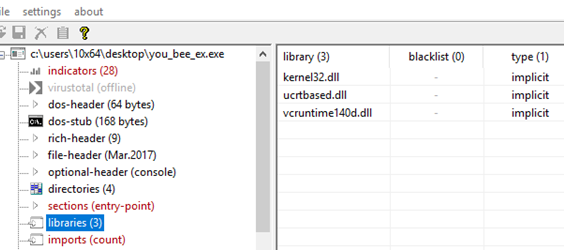
As we can see in the next image, sections show that there is a big difference between raw-size and virtual-size which means the executable is packed...
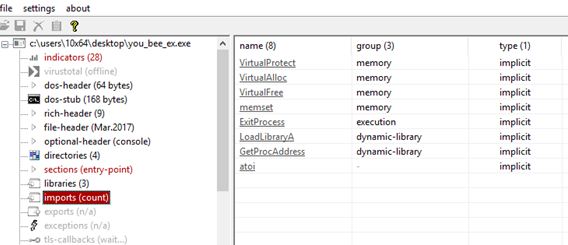
Checking imports and libraries but nothing new:
4. Capa
By identifying the capabilities in our executable using Capa to know more about its behavior:
I didn’t get anything new but now I know the executable is packed, Nice!
What a new and interesting something -_-
Let’s go for Basic Dynamic Analysis to know more about its behavior
2- Basic Dynamic Analysis
Run the executable and check Procmon but there is nothing..
So I should go for Advanced Static Analysis now...
3-Advanced Static Analysis
Using IDA to check the instructions and search for anything interesting but before this we should unpack the executable
We can unpack it by UPX tool, check the next image:
Let’s Open IDA...
By following the main function we got that:
The function takes some arguments and then checks if they are between 100 and 105 and if true then it will get the pass of the file by GetModuleFileNameAAPI...
After that it will xor all characters from the path with a constant value then print the encoded strings.
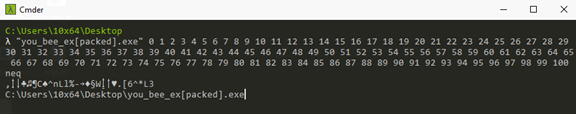
Let’s try to pass 101 arguments to the packed and unpacked files to see what happens:
we got different results from the 2 files.
As we know the GetModuleFileNameA API get the pass of the executable so we can debug the packed file, follow the API, get the pass, and then patch it with the original pass.
We can get the original path from the unpacked file by Strings :
This is the original pass:
C:\Users\11x256\documents\visual studio 2015\Projects\ConsoleApplication1\Debug\ConsoleApplication1.pdb
4-Advanced Dynamic Analysis
Let’s debug the packed one with x32dbg and follow the API...
We should add the arguments to the command line of the program first, you can do it from File > Change Command Line
And then add the arguments as the next image:
Now set the API as a breakpoint by adding bp GetModuleFileNameA to command here:
After running, it will break at the API as the next image:
We don’t need to know what happened in the API so just click on ‘execute till return’ and we will get that:
Step over one time to get this:
Let’s understand it now,
If u back to IDA you will see the same cmp instruction here:
And we can get that [ebp-14] before it in the last image in x32dbg will be the pass of the file in our system, so we can get the value of the pass by follow its value in the dump like the next image:
And we got it:
Now we can patch the pass and add the original pass that we get from strings before, just right click on the pass > Binary > Edit :
We will get this window:
Now just change the pass value
C:\Users\10x64\Desktop\you_bee_ex.exe
With the original one:
C:\Users\11x256\documents\visual studio 2015\Projects\ConsoleApplication1\Debug\ConsoleApplication1.pdb
And press OK :
Notice the change here:
Ok if we just scroll back some lines we will get the xor instruction:
So we can click on ‘execute till return’ to see what will return:
Check the program console and...
Yes we got the **** flag! x_x
OK there are another methods you can solve the challenge with them like getting the tail jump and get the OEP (Original Entry Point) in x32dbg, then by using Scylla plugin to fix the OEP and check the executable in IDA but it will take more time than the debugging method here, So you can solve it by different ways .
Sorry for my English btw xD
Good Luck <3